HoneyPot : Intrusion Detection and Malware analysis
This is a Guest Post by “Satyajit Das” , who is an Ethical Hacking enthusiast & shares his tips about security at Security Hunk
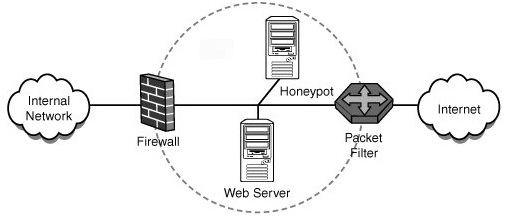
What is the HoneyPot ?
How to install a HoneyPot?
There are many software package available under this name but here we will discuss about Honeybot and Kfsensor.
Step 1.First download Honeybot – Click Here and install it in your box.
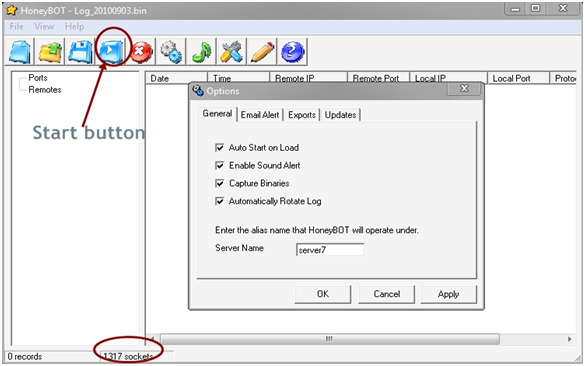
Step 2.Now open up it and click on the start button and wait for all the sockets to load(see at the bottom).
Step 3.Having done that click on option and configured to your convenience or as show below.
Step 4.You can see the View option to set few more settings. Now the honeybot is configured and just minimize to system tray.
Step 5.Once few result start appearing then you can right click on a particular result to see the details or even do a reverse DNS as shown below.
There is another software-Kfsensor which is a shareware but the trail version is available. You need to install WinPcap latest version before you install this package.I would prefer using Kfsensor compared to Honeybot as it has got more details evaluation options.
One can also view the ports accessed by the attacker as shown below by selecting the view port option.
HoneyPot surely can be used for intrusion detection and malware analysis in secure the system from future attacks but still then I would repeat the line which is one of the fav among the hackers community is “still then it can be hacked”….yeah there are methods by which the presence of a honeypot can be detected and by that one can avoid the trap set for him/her.Research is still on in this field and hope some advanced features would come up.





![Bypassing Wi Fi HotSpot Access Control By Session Stealing [Hacking]](https://hackersenigma.com/wp-content/uploads/session-hijacking-wifi-hotspot-80x65_c.jpg)



2 Comments
The article is really nice, but it needs more effort, You should have also demonstrated how to set up a honeypot to trap Hackers
Rafay
Thanks that you liked it… :)…….yeah..thats true..but this is only for noobs to make them understand the basics of honeypot. 🙂